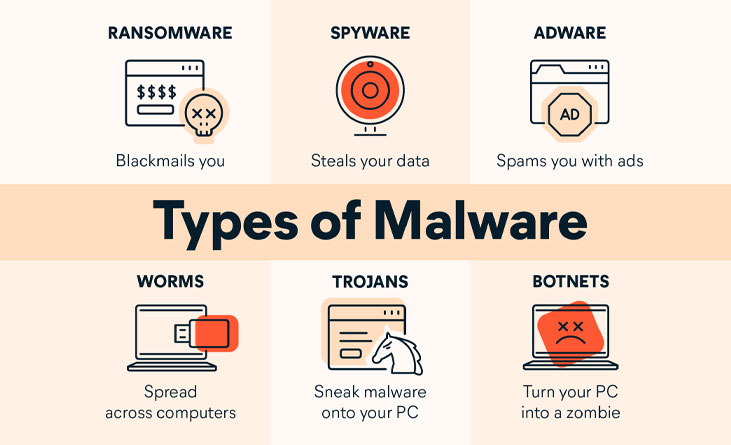
Cybercriminals use malware to steal data, encrypt files, and disrupt business processes. Understanding the different types of malware can help businesses protect their systems and devices from malicious attacks.
Malware can be delivered through phishing emails, malvertising, visiting infected websites, or exploiting vulnerabilities. Some examples of malware include viruses, worms, Trojan horses, and spyware.
Polymorphic Malware
So, what is malware on a computer? Polymorphic malware is a modern digital threat that can be difficult for traditional blacklist antivirus software to detect. It uses advanced coding techniques, including code obfuscation and incorporation of useless code, to make it harder for security software to recognize its signatures.
These viruses can encrypt files, corrupt programs, and delete data. They can also spoof computer hardware such as webcams and microphones to steal information like usernames and passwords. They can even take over a device or network to attack other computers and demand ransom.
To combat this type of malware, businesses can use heuristic and behavior detection tools. This can help prevent infections from being triggered by suspicious actions, such as unusual requests for passwords or misdirection of the browser to unknown websites. Companies can also stay one step ahead of cybercriminals by following tried and true cybersecurity best practices and updating their security software. This includes installing the latest patches and using a firm password policy.
Viruses
Viruses are self-replicating computer programs that infect other systems, steal data, or hold computers hostage. They spread through phishing, malvertising, visiting infected websites, or exploiting vulnerabilities. They cause downtime, data breaches, and intellectual property theft. Some viruses require payment in cryptocurrencies such as Bitcoin to unlock the system or its data.
Trojan horses, also known as backdoors, give cyber attackers access to a computer. These malware programs open doors to the attackers, enabling them to install more sophisticated hacking tools such as adware or spyware. They can be detected by slowing a computer’s performance, consuming unusual bandwidth, or freezing and crashing.
Some viruses attack specific systems, like the Melissa virus that infected Microsoft Outlook users in 1999 and sent itself to the first 50 people in their contact list, or the CryptoLocker ransomware virus that encrypted victims’ files and demanded payment to regain access in 2017. Other viruses target users with political or social messages, such as the Stoner virus 2014, which displayed on-screen messages supporting marijuana legalization. Polymorphic viruses continuously change their underlying code to avoid detection by antivirus software or digital forensics.
Trojans
Taking their name from the hollowed-out wooden horse the Greeks used to smuggle soldiers into Troy, Trojan malware uses deception and social engineering tactics to trick users into running seemingly harmless software that conceals malicious codes. Unlike viruses and worms, which attach themselves to other programs, Trojan malware operates independently.
Some Trojans mimic popular video games, practical applications, and antivirus software to entice unsuspecting users into downloading them. Others, like ransom Trojans and cryptojacking Trojans (which steal device resources to mine cryptocurrency), can hold user data hostage or slow down computer systems until users pay a financial fee to unlock them.
Trojans often hide in third-party app download sites and manipulate email attachments or links. However, they can also use unpatched vulnerabilities and weak security defenses to infect devices directly. Telltale signs of Trojan infection include computer settings changing or the device suddenly slowing down. More sophisticated variants, like the Rakhni and Tiny Banker Trojans, have even been used to deliver ransomware and steal user financial credentials. Infected devices can remain undetected for months before users notice any changes.
Botnets
Botnets are groups of infected computers, often called bots, managed remotely by cybercriminals. They can be used for malicious activities such as sending spam emails, stealing passwords, or launching attacks against websites and networks.
Computers can be recruited into a botnet by clicking on an infected link in a phishing email, downloading a drive-by download, or exploiting a vulnerability found in a web browser. Once a bot has been installed, it will monitor for instructions distributed from its controlling server (known as a C2) and carry out those commands.
Bots are an excellent way for bad actors to increase, automate, and speed up attacks. Distributed denial of service, or DDoS attacks, for example, are impossible to launch without the help of bots. Bots can also be employed for automated password attacks by using breached credentials, dictionaries, or brute force to seize the passwords of online accounts.
Mobile Malware
The proliferation of smartphones, tablets, and smartwatches creates a tempting honeypot for attackers. Mobile malware includes viruses, worms, Trojans, spyware, and more. This type of malware attacks the operating systems of mobile devices and can steal or disrupt data, applications, passwords, and other sensitive information.
Infections of mobile devices can result in financial fraud, privacy breaches, and slowed productivity. Using overlay attacks to steal logins and credit card information and taking control of devices remotely, hackers can commit unauthorized transactions or even drain bank accounts.
Hackers can spread mobile malware by hiding malicious code in apps available for download from app stores or third-party websites. These apps often appear legitimate but were developed for malicious purposes such as stealing OTP, making online transactions, or spreading spyware.
Mobile malware can also hide behind ad campaigns to distribute spyware and other malware variants on users’ devices. For example, the Android-based Joker malware uses invisible ads on social media sites to send users to infected web pages that will download more malicious software.


Pingback: Leveraging Managed Services For Business Continuity Planning - Tech&Trends